Cyber Incident Response Specialist I Salary in the United States
Cyber Incident Response Specialist I Salary
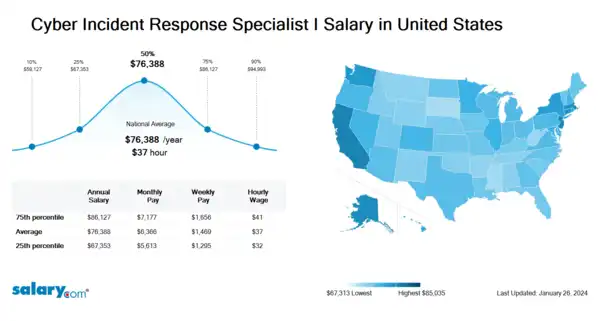
How much does a Cyber Incident Response Specialist I make in the United States? The average Cyber Incident Response Specialist I salary in the United States is $76,804 as of March 26, 2024, but the range typically falls between $67,371 and $86,666. Salary ranges can vary widely depending on many important factors, including education, certifications, additional skills, the number of years you have spent in your profession. With more online, real-time compensation data than any other website, Salary.com helps you determine your exact pay target.
| Percentile | Salary | Location | Last Updated |
| 10th Percentile Cyber Incident Response Specialist I Salary | $58,782 | US | March 26, 2024 |
| 25th Percentile Cyber Incident Response Specialist I Salary | $67,371 | US | March 26, 2024 |
| 50th Percentile Cyber Incident Response Specialist I Salary | $76,804 | US | March 26, 2024 |
| 75th Percentile Cyber Incident Response Specialist I Salary | $86,666 | US | March 26, 2024 |
| 90th Percentile Cyber Incident Response Specialist I Salary | $95,644 | US | March 26, 2024 |
Cybersecurity Engineer (OH) [JOB ID: 20240425]
Phoenix Cyber - Blacklick, OH
PSM Partners - Cleveland, OH
The Newberry Group - Columbus, OH
Plaskolite Inc - Columbus, OH
- View Hourly Wages
-
Select State
-
Select City
-
Choose Similar Job
-
Pick Related Category
- View Cost of Living in Major Cities
What skills does a Cyber Incident Response Specialist I need?
Each competency has five to ten behavioral assertions that can be observed, each with a corresponding performance level (from one to five) that is required for a particular job.
Analysis: Analysis is the process of considering something carefully or using statistical methods in order to understand it or explain it.
SIEM: Security information and event management is a field within the field of computer security, where software products and services combine security information management and security event management.
Network Security: Network security consists of the policies and practices adopted to prevent and monitor unauthorized access, misuse, modification, or denial of a computer network and network-accessible resources. Network security involves the authorization of access to data in a network, which is controlled by the network administrator. Users choose or are assigned an ID and password or other authenticating information that allows them access to information and programs within their authority. Network security covers a variety of computer networks, both public and private, that are used in everyday jobs; conducting transactions and communications among businesses, government agencies and individuals. Networks can be private, such as within a company, and others which might be open to public access. Network security is involved in organizations, enterprises, and other types of institutions. It does as its title explains: It secures the network, as well as protecting and overseeing operations being done. The most common and simple way of protecting a network resource is by assigning it a unique name and a corresponding password.
Job Description for Cyber Incident Response Specialist I
Cyber Incident Response Specialist I investigates, reports, and responds to detected cyber incidents. Maintains system cybersecurity monitoring operations, and performs cyber incident triage to determine scope, urgency, and potential impact of the incident. Being a Cyber Incident Response Specialist I identifies the specific vulnerability and makes recommendations for remediation. Proactively searches for threats using a variety of Computer Network Defense (CND) tools, including intrusion detection system alerts, firewall and network traffic logs, and host system logs. Additionally, Cyber Incident Response Specialist I documents all activities that occurred during the incident using established methodologies and procedures. Conducts a root cause analysis for each incident to define follow-up action items and to make recommendations to stakeholders. Develops and maintains thorough, up-to-date knowledge of cybersecurity threats and incident response best practices. Typically requires a bachelor's degree in computer science. Typically reports to a manager. The Cyber Incident Response Specialist I work is closely managed. Works on projects/matters of limited complexity in a support role. To be a Cyber Incident Response Specialist I typically requires 0-2 years of related experience. (Copyright 2024 Salary.com)... View full job description
See user submitted job responsibilities for Cyber Incident Response Specialist I.
Search Job Openings
Salary.com job board provides millions of Cyber Incident Response Specialist I information for you to search for. Click on search button below to see Cyber Incident Response Specialist I job openings or enter a new job title here.
Career Path for Cyber Incident Response Specialist I
A career path is a sequence of jobs that leads to your short- and long-term career goals. Some follow a linear career path within one field, while others change fields periodically to achieve career or personal goals.
For Cyber Incident Response Specialist I, the first career path typically starts with a Cyber Incident Response Specialist II position, and then progresses to Cyber Incident Response Specialist IV.
Additionally, the second career path typically progresses to Incident Response Manager.
What does a Cyber Incident Response Specialist I do?
Are you an HR manager or compensation specialist?
Salary.com's CompAnalyst platform offers:
- Detailed skills and competency reports for specific positions
- Job and employee pricing reports
- Compensation data tools, salary structures, surveys and benchmarks.

Cyber Incident Response Specialist I Pay Difference by Location
Cyber Incident Response Specialist I salary varies from city to city. Compared with national average salary of Cyber Incident Response Specialist I, the highest Cyber Incident Response Specialist I salary is in San Francisco, CA, where the Cyber Incident Response Specialist I salary is 25.0% above. The lowest Cyber Incident Response Specialist I salary is in Miami, FL, where the Cyber Incident Response Specialist I salary is 3.5% lower than national average salary.
| City, State | Compared to national average |
|---|---|
| City, State San Francisco, CA |
Compared to national average
|
| City, State Washington, DC |
Compared to national average
|
| City, State Miami, FL |
Compared to national average
|
| City, State Chicago, IL |
Compared to national average
|
| City, State Boston, MA |
Compared to national average
|
| City, State New York, NY |
Compared to national average
|
| City, State Dallas, TX |
Compared to national average
|
Similar Jobs to Cyber Incident Response Specialist I

| Job Title | Experience | EDUCATION | Salary Compared to This Job |
|---|---|---|---|
| Job Title Cyber Incident Response Director | Experience | EducationBachelors | Salary Compared to This Job |
| Job Title Cyber Incident Response Manager | Experience 5 + | EducationBachelors | Salary Compared to This Job |
| Job Title Cyber Incident Response Senior Manager | Experience | EducationBachelors | Salary Compared to This Job |
| Job Title Cyber Incident Response Specialist II | Experience 2 - 4 | EducationBachelors | Salary Compared to This Job |
| Job Title Cyber Incident Response Specialist III | Experience 4 - 7 | EducationBachelors | Salary Compared to This Job |
Level of Education for Cyber Incident Response Specialist I
Jobs with different levels of education may pay very differently. Check the Cyber Incident Response Specialist I salary of your education level.
- Cyber Incident Response Specialist I Salaries with No Diploma
- Cyber Incident Response Specialist I Salaries with a High School Diploma or Technical Certificate
- Cyber Incident Response Specialist I Salaries with an Associate's Degree
- Cyber Incident Response Specialist I Salaries with a Bachelor's Degree
- Cyber Incident Response Specialist I Salaries with a Master's Degree or MBA
- Cyber Incident Response Specialist I Salaries with a JD, MD, PhD or Equivalent
Cyber Incident Response Specialist I Salary by Global Country
Cyber Incident Response Specialist I salary varies from country to country. There are several factors that mainly impact the Cyber Incident Response Specialist I salary, including cost of living, economic conditions, market rates and legal differences. Click below to Cyber Incident Response Specialist I salary of the other country.
Cyber Incident Response Specialist I Salary by State
Geographic variations impact Cyber Incident Response Specialist I salary levels, due to various factors, such as cost of living, industries, market demand and company budgets. Click below to see pay differences between states.
Browse All IT - Networking Jobs by Salary Level
Browse Related Job Categories With Cyber Incident Response Specialist I
A job category is a classification or grouping of job positions that share similar characteristics, functions, or industries. Cyber Incident Response Specialist I salary varies from category to category. Click below to see Cyber Incident Response Specialist I salary in different categories.
Take just three simple steps below to generate your own personalized salary report
Understand the total compensation opportunity for a Cyber Incident Response Specialist I, base salary plus other pay elements
Average Base Salary
Core compensation
Average Total Cash Compensation
Includes base and annual incentives
View the Cost of Living in Major Cities
Skills associated with Cyber Incident Response Specialist I: Vulnerability Assessment, Data Loss Prevention, Security Information and Event Management (SIEM) Software, Incident Management ...More
Recently searched related titles: Cyber Forensics Analyst
Recently searched related titles: Cyber Forensic Analyst, Cyber Operations Specialist, Contact Tracer Supervisor
Jobs with a similar salary range to Cyber Incident Response Specialist I : Incident Management Analyst, Incident Response Analyst, Incident Analyst, Cyber Threat Analyst
Salary estimation for Cyber Incident Response Specialist I at companies like : Homeschool Iowa Convention, Shedpro Co, Guichet Desjardins - Centre automatiseVieux - Québec